Strength of Deep Learning-based Solutions to Secure Healthcare IoT: A Critical Review
Abstract
Healthcare applications of IoT systems have gained huge popularity across the globe. From personal monitoring to expert clinical diagnosis, healthcare IoT systems have shown their importance to all possible extents. The ease of use and precise results add to the wide acceptance of such systems. However, this has also led to a magnificent increase in the number of attacks aimed at stealing or manipulating data as well as operations of HIoT-based healthcare assistance. Among the various modes of attacks, network-based attacks are found in the majority. In this work, we perform a critical review of these attacks, the existing countermeasures, and their limitations to understand and proclaim the importance of securing healthcare networks in the best possible manner. We also emphasize the necessity of deep learning-based smart solutions for securing healthcare systems, understanding the potential of deep learning in the security aspects being deployed in other genres of IoT applications. A comparative analysis of deep learning and machine learning-based security solutions is performed to examine their performances.
1. INTRODUCTION
Over the past decade, technology has grown exponentially, owing to the wide range of applications offered by Artificial Intelligence, the Internet of Things, etc. Healthcare sector has received a greater advantage in this aspect. The Internet of Things has taken over many procedures and also offers remote operations, which were earlier tedious and conducted on the premises of the medical practitioner. With the rapid and widespread acceptance of the Internet of Things in the healthcare sector (HIoT), the healthcare sector has taken a global phase shift.
Hegde et al. (2021) [1] performed an extensive survey on various smart monitoring systems offered to the healthcare sector using IoT. This article provides a basic idea of the operational behaviors of healthcare IoT systems. Healthcare IoT [2] based systems can be broadly classified into two subcategories, namely personal HIoT and clinical HIoT, based on their level of application. Personal HIoT mainly includes wearable devices, such as activity/heart-rate trackers, smart clothes, and smartwatches that are used for self-monitoring. These are meant to be adopted for regular monitoring and come without any expert-level guidance, except that is given along with the product. On the other hand, clinical HIoT devices are developed specifically for health monitoring and have to be used with the guidance and involvement of a medical practitioner, for example, glucose monitors, connected inhalers, etc. Clinical IoT systems are often set up in clinical environments. Clinical IoT systems which are used in home environments have to be regulated and approved for use only after clinical validation.
Healthcare IoT (HIoT) has helped to reduce the geographical limitations that restrict people from experiencing expert consultation significantly. It has also made regular check-ups remotely operable. The user-friendly nature of these assistive mechanisms offered by HIoT has added more to its widespread use and popularity. Such systems have great strength, especially during the pandemic times. Along with the widespread popularity and acceptance comes the increased risk of malicious attacks [3]. The sensitive nature of the contained information attracts attackers owing to the impact of a successful attack. The consequences of such an attack can even include the death of the patient. Hence, it is really important to safeguard the HIoT systems and their contained information.
Attacks on healthcare IoT systems [4] can be classified into various categories based on the nature of the attack, the surface of the attack, and the mode of attack. There are active attacks and passive attacks. The passive attack tries to steal the information without taking a chance to modify it, while active attacks try to alter the information or change the device configuration and other modifications to the system. There are internal and external attacks, where internal attacks are triggered by some internal participants of the system, and external attacks are launched from outside the system boundaries. There are physical attacks [5], datalink attacks, network attacks, transport attacks, and application attacks based on the area of attack. Attacks on healthcare IoT systems mainly include denial of service, man-in-the-middle attacks, replay attacks, jamming attacks, tampering attacks, Sybil attacks, synchronization attacks, etc. Many solutions have been proposed in order to tackle the attacks on healthcare IoT.
In this review, we perform a critical review of some of these solutions, focusing on works that address network-based attacks over healthcare IoT systems. We discuss various attacks against healthcare IoT systems, the privacy concerns in healthcare IoT, countermeasures suggested to tackle the attacks and the importance of deep learning applications in these aspects. The remaining part of the paper is organized as follows: section 2 summarises related literature with subsections that discuss the classification. Section 3 details the analysis and inferences, and section 4 concludes the work.
2. RELATED LITERATURE
Several papers related to our topic of discussion were reviewed. However, in this section, we summarize some important articles that had major contributions to our work. We have classified the summary into various subsections to provide a better understanding of the same.
2.1. Surveys on Security Challenges
Kolandaisamy et al. (2021) [6] discussed the security risks associated with IoT-based healthcare networks. They analyzed various attack modes, architectural differences, and various technologies that are designed to secure these systems. The architectural layers of the IoT environment were also explained, providing an insight into what and where the vulnerabilities are in each layer.
Sengupta et al. (2020) [7] performed a detailed survey on various attacks, security vulnerabilities, and viable block-chain based solutions that can be used to tackle these issues. The authors categorized and also performed a comparative analysis of earlier surveys in this area and consolidated various attacks on IoT networks and their variant characteristics.
Iqbal, et al. (2020) [8] reviewed the important threats, challenges, security requirements and viable countermeasures in the IoT generalized context. Threats like social engineering-based vulnerabilities, user unawareness, hardware vulnerabilities, denial of service attacks, their variants, etc., bring a huge risk to these IoT-based systems. Attacks on each layer of the IoT system were discussed in the article. Default security mechanisms might fail to address those trials, which include code modification, updated malware definitions, etc. They suggested software-defined security for better safety of IoT systems.
Challenges to IoT applications are mainly classified as hardware-based, software-based and network-based, as defined in a study conducted by Mohammad et al. (2019) [9]. Attacks on these systems are mainly aimed at either taking control of the system or stealing the contained information. The authors of the article also performed a case analysis on various types of attacks that target the different applications of IoT, like healthcare, smart cars, smart campus, smart farms, etc. Cilleruelo et al. (2021) [10] presented the security and privacy issues found across data-over-sound devices used in healthcare IoT systems. They suggested a reverse engineering-based method to analyze the security challenges in the system, thereby enabling suitable countermeasures. Ali and Mahmoud (2019) [11] mentioned various routing attacks found in healthcare IoT-based networks. Black hole attacks and delay attacks are explored in detail, and the authors also proposed a preventive mechanism that employs both presence and absence of AODV protocol. However, it could produce only a slight improvement in the system's performance.
Somasundaram and Thirugnanam (2021) [12] studied various security issues found in IoMT systems. They assessed the risks associated with IoMT-based systems by considering the probability and possible impact of the attacks. The possibility of an attack is related to the vulnerability levels of the medical device. The assessment revealed that DDoS-based attacks have higher impacts on IoMT-based systems. A. Ali and Mahmoud [13]. performed an analysis of the security strengths and challenges in IoT systems that operate in the healthcare environment. They adopted 2 protocols (SecRout and AODV) based on which the assessment was carried out. SecRout uses the symmetric cryptographic organization to ensure data. Its two-layer architecture helps in reducing communication overhead. AODV protocol offers better support for unicast and multicast routing schemes but is more prone to attacks. Table 1 shows the inferences from 2.1.
In this section, we consolidated various studies conducted to identify the security challenges and vulnerabilities in an IoT environment. The number of challenges identified is generic and could be applied to all the application domains of IoT. When the healthcare domain is specifically considered, these challenges send out an alert to safeguard the systems so that the sensitive data and devices are secured from malicious attacks.
2.2. Attacks and Classifications
The authors (Rajendran et al. (2019)) [14] described various threats that are commonly found in IoT systems, classifying them based on the layer of attack, like IoT devices and peripherals, gateways and internal network elements, cloud and related elements. They also tabulated various countermeasures that could be employed to mitigate these threats. Sharma (2022) [15] put forward a solution to detect and prevent any jamming attacks that might be used against IoHT systems. The algorithm developed can analyze the strength of a signal received, the ratio of packet loss, and the number of devices disrupted, which might be the outcome of a jamming attack. This helps in enabling secure communication between IoHT devices and transferring confidential data without any hindrance.
Calvillo-Arbizu et al. (2021) [16] performed an in-depth analysis of the Internet of Things employed in the healthcare sector. They analyzed the scenario over three themes: the lifecycle of data, trust and privacy, and human-related issues. Qadri et al. (2020) [17] elaborated on the increasing popularity and widespread use of IoT systems in various areas, especially healthcare. They also discussed the limitations in the existing security mechanisms from the IoT perspective due to resource constraints. The main threats discussed were selective forwarding and wormhole routing-based attacks. The authors suggested a block-chain based solution to prevent the above-mentioned attacks.
Djenna and Eddine (2018) [18] discussed various cyber-attacks related to a healthcare IoT-based infrastructure. They categorized the threats based on their occurrence and clearly described various attacks, pointing to their distinct characteristics. Ahmed et al. (2018) [19] discussed malicious insider attacks in multi-cloud-based e-healthcare systems. The multi-cloud environment provides a wide range of services for IoT systems and is also vulnerable due to the heterogeneity in working strategies. Malicious insiders are those who take up a role in the environment but misuse it for some benefit. It can also be those agents who put up some actions unknowingly. In the case of the healthcare environment, these can include both service personnel and the persons from the patients’ end. This might lead to manipulation of the sensed data and thereby, a false analysis.
In this section, we consolidated various works discussing the types of attacks against IoT systems. The occurrence of such attacks can result in consequences of varying impacts, according to the application domain (Table 2).
| References | Inferences | Gaps Identified |
| [14-19] | Various modes of attacks were identified. The patterns in attacks, the consequences and some ideas on how to mitigate these attacks were discussed. | The articles fail to provide a solution that is quick enough to detect, prevent and protect healthcare networks from attacks. |
2.3. Privacy Concerns
In their article, Khatkaret al. (2020) [20] discussed in detail the impacts of distributed denial of service attacks on healthcare devices. They classified DDOS attacks into five groups based on the motto of the attacker. The limited resource and capacity constraints of IoT systems make them prone to DDOS attacks. Hence, using inherent security frameworks in IoT systems is of prime importance. Sethuraman et al. (2020) [21] explained how healthcare IoT devices are hacked and malfunctioned using UAVs. Attack modes like de-authentication attacks, stepping stone attacks, evil twin attacks, WiFi-phishing attacks, etc., are also discussed. They also provided an experimental setup to substantiate their findings.
Pu (2020) [22] performed an extensive study on RPL-based security for IoT. The vulnerabilities were analyzed. Then, a GINI-based solution was proposed to prevent Sybil attacks. However, the solution failed to incorporate protection against spoofing attacks. Goel et al. (2019) [23] discussed various attacks against IoT systems, suggested some methods to enhance security, and also explained various security paradigms in this context.
In this section, we reviewed various articles that addressed challenges to the privacy of contained data. Preserving the privacy of sensitive data is of great importance as the impact of a possible data breach would include defaming, misuse, etc. Healthcare data is sensitive in nature, and protecting the privacy of such medical data is a critical task (Table 3).
2.4. Countermeasures
He et al. (2018) [24] presented in their article the necessity of improving the password-based security mechanism for healthcare devices. They illustrated how password-guessing attacks could compromise healthcare devices and steal healthcare data. They also suggested mechanisms to enhance security by adopting strong passwords and also proposed a password-strengthening mechanism.
In their article, Thilakarathne et al. (2021) [25] emphasized the privacy concerns in Medical IoT, focusing on where breaches could occur and why they should be preserved. The scope of privacy and its breaches, the gains of attackers, and also countermeasures to keep privacy intact were discussed in the article.
Ranjith and Mahantesh (2019) [26] conducted a collective analysis of various security mechanisms currently employed in smart healthcare systems. Security mechanisms adopted, like attribute-based access control, lightweight authentication, opportunistic computing, context-based, etc., were discussed. Issues like secure authentication, DDoS, inner device authentication, key management, etc., were also explained.
Fazeldehkordi et al. (2019) [27] performed an extensive case study on the security and privacy aspects of healthcare products. The analysis was carried out based on various criteria like connectivity, protection, etc. They selected pacemaker security and privacy as the prime subject of analysis and discovered that their proposed security framework enforced better security and privacy for the pacemaker. However, the chances of spoofing-based attacks and DoS attacks were not properly addressed in the article.
Alladi and Chamola (2020) [28] proposed a solution to enforce security against physical attacks in healthcare IoT networks like tampering and/or replacement of collaborating nodes. They suggested using an advanced protocol that employs physical unclonable functions (PUFs), which enforce session key uniqueness and secrecy.
Rughoobur and Nagowah (2017) [29] formulated a framework that detects replay attacks, where the attacker gets hold of the network traffic, acts as a legitimate sender and sends modified packets to the receiver. The framework is formulated using a combination of universally unique identifiers, timestamps and a self-learning battery depletion rate monitor. However, the denial of service attacks was not addressed.
Ge et al. (2019) [30] elaborated on a deep learning-enabled solution to detect intrusions in IoT networks. They used the BoT – IoT dataset to retrieve the network-related information and train the system. Features were extracted from the field information and processed to identify potential intrusions.
Vithanwattana et al. (2021) [31] suggested a new security framework to enhance the security and privacy of the contained information in healthcare systems. It offered some key services, like encryption as a service, capabilities or tokens to do specific tasks, a storage management system, digital filters to restrict access levels, secure modes of transport and transaction, etc. (Table 4).
Various countermeasures have been proposed for attacks against IoT devices, particularly in the healthcare domain. The need to enhance current security mechanisms was discussed in all the articles.
3. ANALYSIS AND INFERENCES
This section presents a consolidated description of our inferences after reviewing the current trends in healthcare IoT security mechanisms. We analyzed articles published in the past 5 years on related topics. The section is organized in a sequential mode to give a better understanding to the reader. We will first examine the attack patterns over healthcare IoT networks and the strength of existing methods and then discuss them in terms of deep learning-enabled technologies. The subsections are arranged accordingly.
3.1. Attacks over Healthcare IoT
Fig. (1) gives an analysis of the occurrences of various network attacks. Tables 5a and b presents the consolidated hierarchical outlook of attacks aimed on healthcare IoT systems. According to recent surveys, 42 percent of these attacks were over or through the network, 33 percent over physical devices and controllers, and the remaining through other modes of attacks.
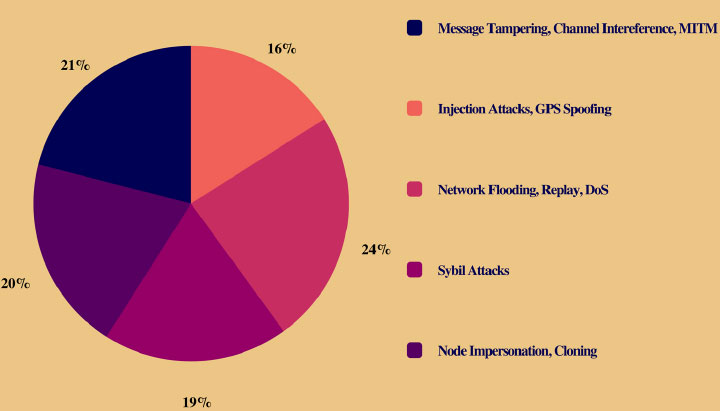
| References | Inferences | Gaps Identified |
| [24-31] | Recent enhancements in security measures to protect IoT networks are examined. The efficiency of such mechanisms is discussed. | The articles focused only on securing against a specific mode of attack. They did not analyze the possibilities of combined attacks. |
| Attacks on Healthcare IoT devices | Area of Attacks | Physical Layer | Malware, RFID spoofing, cloning, physical damage/ alteration |
| DataLink Layer | Traffic analysis, MITM, DoS, spoofing, cloning | ||
| Network Layer | IP attacks, sniffing | ||
| Application Layer | Session hijacking, XSS, SQL injection, HTTP-based attacks |
| Attacks on Healthcare IoT devices | Target of Attacks | Access | Spoofing, password attacks, cloning |
| Data | Phishing, sniffing, social engineering, cryptanalysis | ||
| Controllers | Tampering, DoS, DDoS, jamming, node-based injections | ||
| Networks | Replay attacks, Sybil attacks, IPv6 attacks, MiTM, Network Visualization |
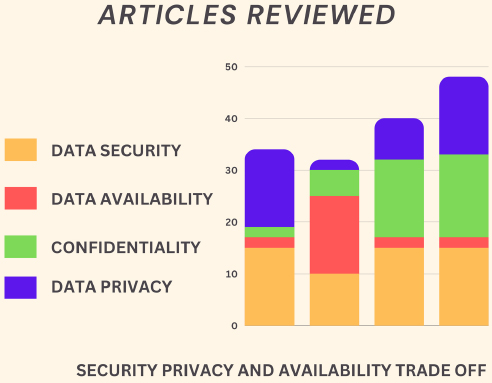
3.2. Analyzing Current Security Solutions
Fig. (2) illustrates the current solutions proposed to protect the HIoT systems.
It indicates whether a particular solution offers the key features of confidentiality, data privacy and availability. These broad classifications will include the integrity of the system and its contained information, availability of the service, authenticity and authorized access.
The articles reviewed in this work addressed one or more of the security concerns in healthcare IoT. However, network attacks in the majority need better attention, and the sensitive information contained demands quick responses.
3.3. Why Use Deep Learning-Based Solutions?
Deep learning is a new artificial intelligence method, which employs algorithms over multiple layers of neural networks. Unlike machine learning, deep learning uses both structured and unstructured learning to build the system, thus providing better accuracy in its predictions. Deep learning has found its application in the healthcare domain in various ways like early disease detection, human behavior recognition, smart device-based detection and analysis of vitals, medicine recognition, etc. However, its applications in the security part of healthcare IoT are minimal.
Deep learning emerged as a promising research area in the past decade. The accuracy levels of deep learning compared to that of machine learning have contributed more to its increased popularity and acceptance. The security measures supported by deep learning include detection, analysis, and prevention. By incorporating deep learning in securing IoT systems, we can enforce better privacy of contained information. Fig. (3) compares the performances of deep learning and machine learning in security aspects.
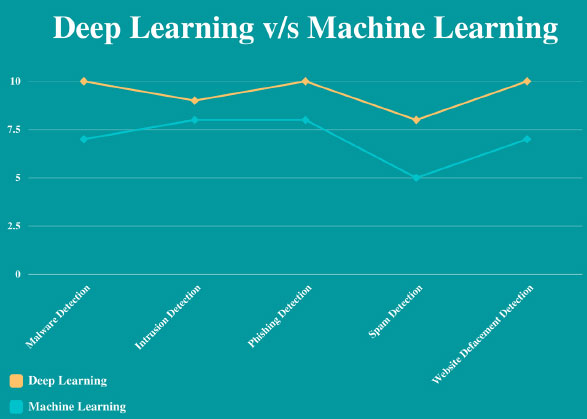
We could find only a few articles [31-39] addressing the security concerns of IoT using deep learning. The primary goals of security, like confidentiality, availability and privacy of the data, are addressed in different articles, but not all in one. The modern modes of network attacks, like distributed denial of service, spoofing, etc., are to be tackled well [40-47]. The network-related attacks have to be addressed systematically owing to the lethality of consequences if found successful. This can range from the wrong diagnosis to even the death of a patient.
As shown in Fig. (3), we compared the machine learning and deep learning-based solutions [48-55] employed for security and privacy concerns. It was found that deep learning-based solutions had a slightly better performance in all the aspects we had considered. Hence, we suggest deep learning-based systems for better accuracy in the early detection of occurrence, thereby preventing it.
CONCLUSION AND FUTURE WORKS
The healthcare industry has grown long and wide by introducing IoT-enabled devices. The widespread popularity is owed to the ease of use and self-monitoring capacities offered by these smart systems. Attacks targeting healthcare IoT systems have also exponentially increased as a byproduct. The sensitive nature of contained information is the prime reason for attacking healthcare systems. The still incomplete transition from the conventional mode of healthcare operations adds more risk to the data contained in the network. In this work, we conducted a critical review of the security concerns of healthcare IoT. Possible attacks, current countermeasures, limitations, etc [56-71]. were studied and analyzed. We reviewed the recent articles published in this area and found that deep learning-based intelligent applications also have to address the security part of the system, thus enhancing its efficiency. The works addressing security concerns fail to provide a holistic solution. Hence, we have identified the necessity of such a system that can act as a healthcare monitor and support mechanism, along with an added security feature that helps to safeguard the data.
Securing healthcare and other sensitive networks has always been an interesting topic for researchers. The currently available security mechanism has an extensive computation requirement, which counts as an extra overhead. Designing a lightweight yet efficient security framework for healthcare systems has also been proposed by various authors. However, incorporating the capacities of deep learning in securing sensitive healthcare data and networks still needs extensive research. Hence, the proposed future research directions include identifying new pitfalls in network security of healthcare IoT systems, checking the possibilities of employing deep learning to secure the system, and finding out a cost-effective solution that can handle the same. Our future works include designing a suitable security algorithm that helps in quick and prompt authentication for healthcare devices, analyzing the performance and computation trade-off, and then refining our work to provide a lightweight, efficient solution to the security of healthcare IoT devices.
LIST OF ABBREVIATIONS
| PUFs | = Physical Unclonable Functions |
| RFID | = Radio-Frequency Identification |
| DDoS | = Distributed Denial of Service |
CONSENT FOR PUBLICATION
Not applicable.
FUNDING
None.
CONFLICT OF INTEREST
The authors declare no conflicts of interest, financial or otherwise.
ACKNOWLEDGEMENTS
Declared none.


